
Multi-Factor Authentication Protect your NWTC account from unwanted access
Account security is a top priority at NWTC. We have implemented multi-factor authentication (MFA) to provide an additional layer of security that makes it harder for cybercriminals to log in to your account.
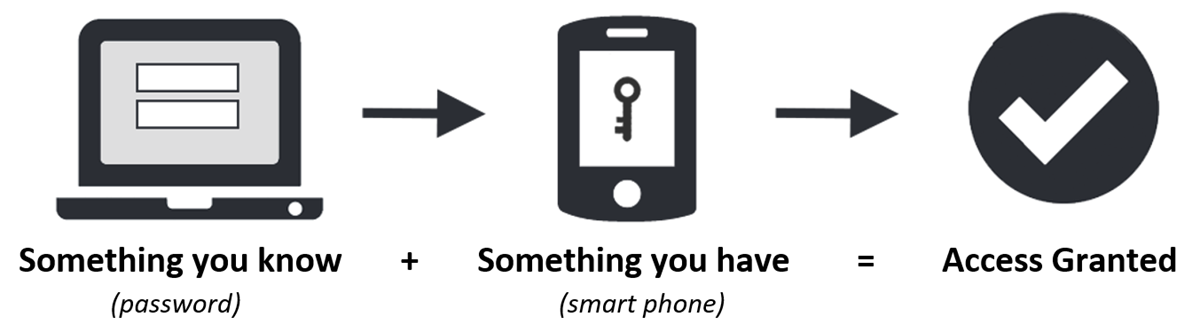
All students and staff must enroll in MFA to access NWTC systems with sensitive information. With MFA, you will use something you know (your password) with something you have (your phone or security key) to confirm your identity when signing in. If a cybercriminal guesses or steals your password, MFA will prevent their sign-in as they do not have access to a device you have (like your phone).
How to set up MFA
There are multiple MFA methods available for students and employees:
Using the Microsoft Authenticator App on your iOS or Android phone
- Browse to My Sign-Ins.
- Click the + Add sign-in method button.
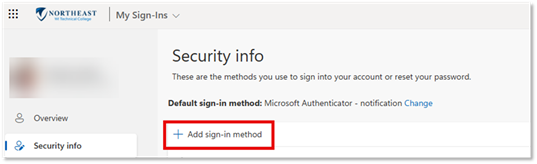
- Click the Microsoft Authenticator button.
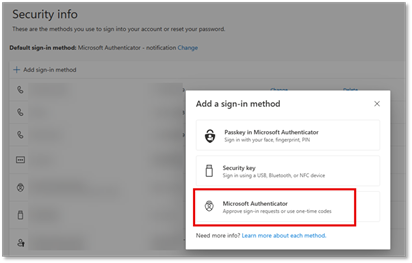
- Click Next.
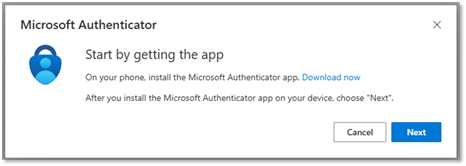
- Stop here on your computer screen and install the Microsoft Authenticator app for your device. View details on how to install the app.
- Open the Microsoft Authenticator app on your device and click the + in the upper right corner of the screen.
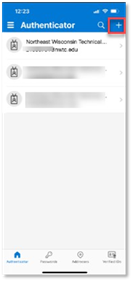
- Select Work or school account.
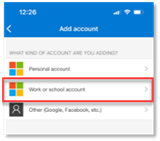
- Click Scan QR code.
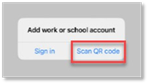
- Open the Microsoft Authenticator app on your device and click the + in the upper right corner of the screen.
- On your computer screen, click Next.
- You will be prompted to set up your account on the Microsoft Authenticator App. Click Next.
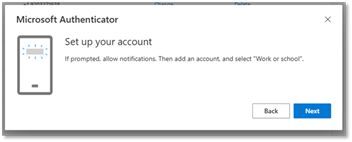
- Use the Microsoft Authenticator app to scan the QR code on your computer screen.
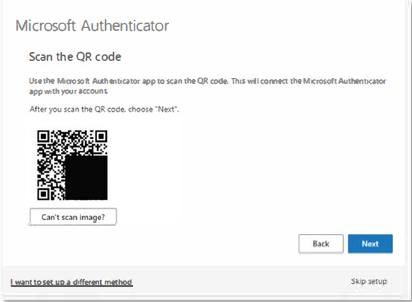
- Click Next.
- You will test your app setup now. Enter the 2-digit code shown on your computer screen into the Microsoft Authenticator app.
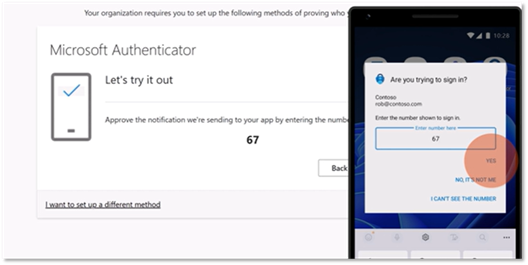
- Click Next on your computer screen.
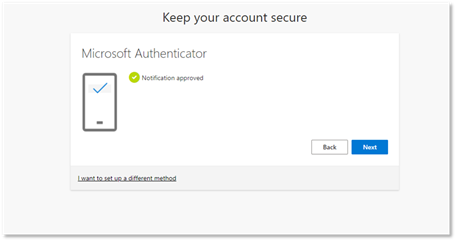
- It should say Notification approved for a successful test. If it does not, choose the back button and try again starting at step 11. If it was successful, click Next on the notification approval page.
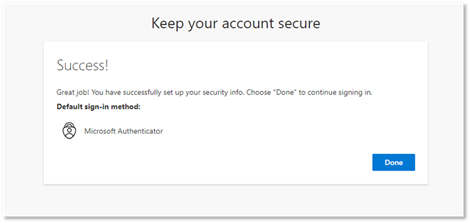
- You have completed enrollment of MFA. Click Done.
Using Phone Call/SMS texting
- Browse to My Sign-Ins.
- Click the + Add sign-in method button.
- Click the box for the type of phone you want to enroll (phone, Alternate phone, or Office phone):
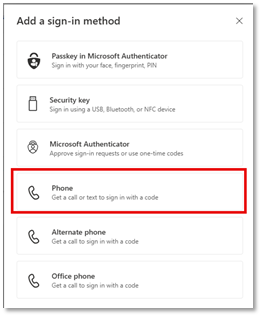
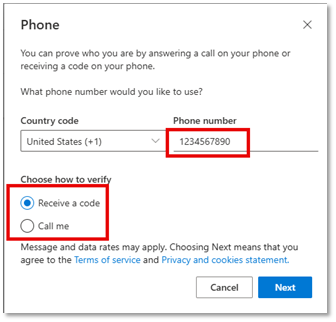
- Enter your phone number with area code into the Phone number box.
- Select Receive a code for text message or select Call me for phone call.
- If you choose Receive a code, you will be prompted to enter it. If you choose Call me, you will receive a call from Microsoft and will need to press the # key on your phone.
- A notification will be displayed confirming that your phone has been successfully registered (if any errors occur return to step 2).
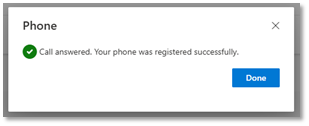
- Click Done.
Frequently Asked Questions
How do I get MFA?
Review the instructions above, then log in to Microsoft with your NWTC ID number@nwtc.edu (example: 12345678@nwtc.edu). Lastly, complete the enrollment of security information.
Do I have to use a smartphone to get MFA?
No; any telephone, Microsoft supported security key, or smart device will work. Students can have a text message sent to their phone. Both staff and students can receive phone calls as a verification. (However, with smart devices, you will get the quickest, simplest experience by enrolling with the Microsoft Authenticator app!) If you are a student who is also a staff member SMS text message will not be a usable MFA method while you are employed by NWTC.
Should I enroll more than one device?
Yes, we encourage you to enroll more than one device so you have a backup if your main device is lost or unavailable. To add additional devices, visit your security options page.
What do I do if I lost my device, left it at home, or am experiencing difficulties authenticating?
Check out these common troubleshooting tips from Microsoft. Call the NWTC Help Desk for assistance. Depending on your circumstance, the Help Desk can either generate a temporary access pass or assist you in configuring another device for MFA.
Is MFA mandatory?
Yes, all NWTC students and employees will be required to enroll in multi-factor authentication (MFA) to provide an additional layer of security for their NWTC account. MFA is an essential element of cybersecurity, and it will aid in protecting everyone’s online information at NWTC. If you do not have the technology to enroll in MFA, reach out to the NWTC Help Desk for support.
I do not have cellular service; how can I log in to my account?
By using the Microsoft Authenticator app, you will be able to use a 6-digit, one-time password code for your account to log in.
What if my account locks out?
If you fail to log in to an MFA protected application more than 10 times without completing the required MFA verification, your account will be temporarily locked out. You may try again to log in after 10-15 minutes or contact the Help Desk for assistance.
Here are some common ways MFA is used every day:
- When using an ATM, you need your debit card (something you have) and your PIN number (something you know).
- When paying for gas with a credit card (something you have) you need to enter your zip code (something you know).
- When logging into your bank account online, you enter your password (something you know), and you are prompted to enter a security code sent to your device via text message or email (something you have).
Important things to remember when using MFA:
- If your second factor device (e.g., your phone or security key) is lost or stolen, report it to the NWTC Help Desk immediately. This helps prevents unauthorized access to your account, and steps can be taken to help you regain access to your account while your second factor device is being replaced.
- Never approve unexpected or suspicious sign-in notifications that you have not performed. If you receive sign-in attempts to your account that you are not performing, reset your password immediately and report the notifications to the NWTC Help Desk.
- Use a screen lock on your phone in case it is lost or stolen. This will help to prevent someone from accessing your MFA device.
Contact Tech Support
Student Help Desk:
Contact the NWTC Student Help Desk for 24/7 assistance.
Staff Help Desk:
Contact the NWTC Staff Help Desk at 920- 498-6800 for assistance, or email help.desk@nwtc.edu to open a ticket in our Staff Help Desk system.